|
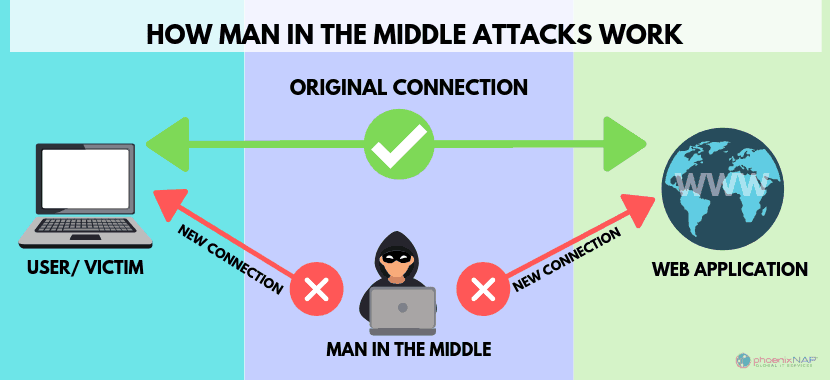
Connecting to an unsecure network? What security risks does a public Wi-Fi connection pose? Here's what you should know. Public Wi-Fi, whether in a public library, coffee shop, train station, or a retail outlet, makes it easy to access the internet anywhere. You can use it to send emails, access your bank accounts, or browse news articles. But should you? Though convenient and desirable for consumers, public Wi-Fi poses security and privacy risks. For instance, free Wi-Fi hotspots don’t need authentication to establish a network connection; this makes it easy for hackers to gain access to unprotected devices on the network. So what are the greatest risks you take when you connect to public Wi-Fi networks? 1. Man-in-the-Middle Attacks When you access the internet via Wi-Fi, your device establishes a link with the router or server connecting you to the internet. A Man-in-the-Middle (MitM) attack occurs when a hacker positions themselves between you and the connection point. So instead of communicating directly with the intended parties, you’re sending your data to the attacker, who then relays it on. Cybercriminals often use special software to view and manipulate the traffic coming in and out of your device. This means they can steal login details, change payment details, or learn where an order is to be delivered. Attackers can also steal your credit card information and commit financial fraud. They can make purchases, withdraw money, and even apply for loans in your name. 2. Malware Infections Hackers can infect an unsecured Wi-Fi connection with malware, which then infects the devices that connect to it. Some attackers can hack the connection point itself and send you fake pop-ups requesting you to update a popular software. Clicking it installs the malware. Once the malware infects your device, the hacker can steal sensitive information, delete files, and make your device inoperable. The worst part is that you might not even notice your device has been infected with malware. 3. Snooping and Sniffing Hackers can eavesdrop on unsecured public Wi-Fi networks. Using special software, an attacker on the network can see what you’re doing on your device while using public Wi-Fi. Sometimes, the hacker will just read your browsing history. If you’re unlucky, the attacker may steal your login details to steal sensitive information resulting in a data breach. Bad actors may also use special software to capture data packets flowing between networked computers. This allows the attackers to capture the information sent across the network, including details like passwords and IP addresses. 4. Evil Twin Attacks The “evil twin” or honeypot attack is a type of attack where a cybercriminal sets up a malicious Wi-Fi hotspot, often intending to steal users’ data. Many people will select a Wi-Fi hotspot if its name sounds appropriate, and almost anyone can set up malicious hotspots that seem legitimate. These hotspots are meant to trick you into connecting to them. Cybercriminals can set up a rogue hotspot and record unencrypted information passing through it. To create the fake access point, attackers usually set up their own “free Wi-Fi hotspots” with the name of a nearby business, like a coffee shop or restaurant. Once you connect your device to the malicious hotspot, the hacker can monitor and steal your personal information, including logins and banking information. The attackers can also perform variations of the MitM attacks, such as DNS-based attacks, forcing you to visit their favorite unencrypted websites. Bottom line: The dos and don'ts of using public Wi-Fi
Do connect to secured public networks whenever possible. In the event that you’re unable to connect to a secured network, using an unsecured network would be permissible if the connection requires some sort of login or registration. Your cellphone hotspot is the best secure connection. Don't access personal bank accounts, or sensitive personal data, on unsecured public networks. Even secured networks can be risky. Use your best judgment if you must access these accounts on public Wi-Fi. Don't leave your laptop, tablet, or smartphone unattended in a public place. Even if you’re working on a secure Wi-Fi network, that won’t stop someone from taking your property or sneaking a peek at your device. Don't shop online when using public Wi-Fi. Sure, shopping doesn’t seem like it involves sensitive data, but making purchases online requires personal information that could include bank account and retailer login credentials. Shopping isn’t something you want to do on an unsecured Wi-Fi network. Do turn off automatic connectivity. Most smartphones, laptops, and tablets have automatic connectivity settings, which allow you to seamlessly connect from one hotspot to the next. This is a convenient feature, but it can also connect your devices to networks you ordinarily would not use. Keep these settings turned off, especially when you’re traveling to unfamiliar places. Do monitor your Bluetooth connectivity. Bluetooth in the home is an amazing feature on many smart devices. However, leaving Bluetooth on while in public places can pose a huge risk to your cybersecurity. Bluetooth connectivity allows various devices to communicate with each other, and a hacker can look for open Bluetooth signals to gain access to your devices. Keep this function on your phone and other devices locked down when you leave your home, office, or similar secured area. Do think about using a virtual private network (VPN) solution to ensure your privacy and anonymity are protected when you use public Wi-Fi. VPN services, like the new Norton Secure VPN, can encrypt all the data that you send and receive while using a public Wi-Fi hotspot, securing your information from other users of the same connection.
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
Archives
November 2023
|
|
2951 Britannia crescent
Port Coquitlam BC, V3B 4V5 778-776-6222 Hours of operation Mon - Fri 9 a.m. - 6 p.m. Sat 11 a.m. - 5 p.m. (by appointment only) Sunday & Holidays - Closed |
Business Number 778569517BC0001 - © Copyright CompuBC, All Rights Reserved.
|