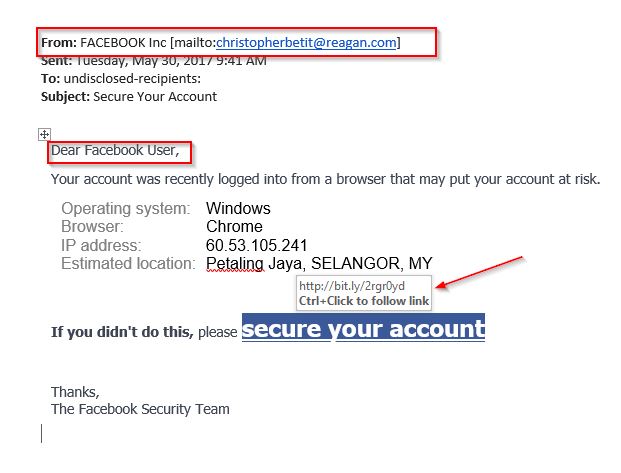
A relatively harmless fake email disguised as an email from Facebook Support provided a primer on signs to look for in identifying emails of the annoying variety, like this one, as well as more serious ones that lead to malware, phishing, or other cyber-security issues.A relatively harmless fake email disguised as an email from Facebook Support provided a primer on signs to look for in identifying emails of the annoying variety, like this one, as well as more serious ones that lead to malware, phishing, or other cyber-security issues.
The email, pictured below, looks like an authentic communication from Facebook Support at first glance, but upon further examination, red flags fly.
The moral of the story: Look for signs like those listed above if there is the slightest reason to be suspicious of emails that appear to be from Facebook but seem a little off.
0 Comments
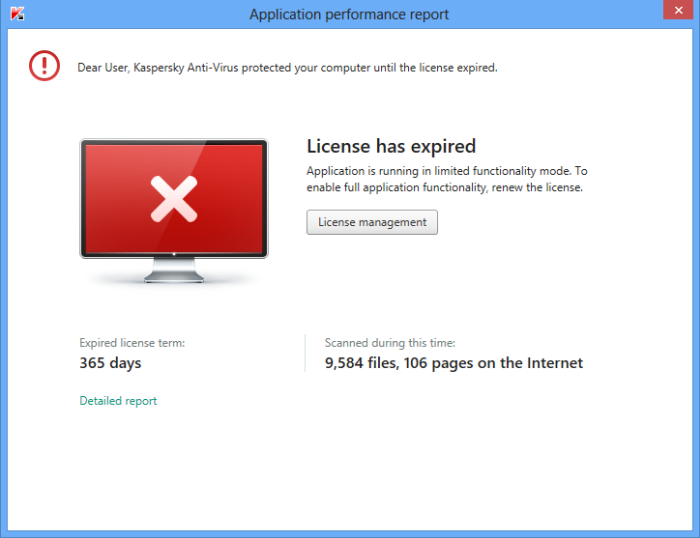
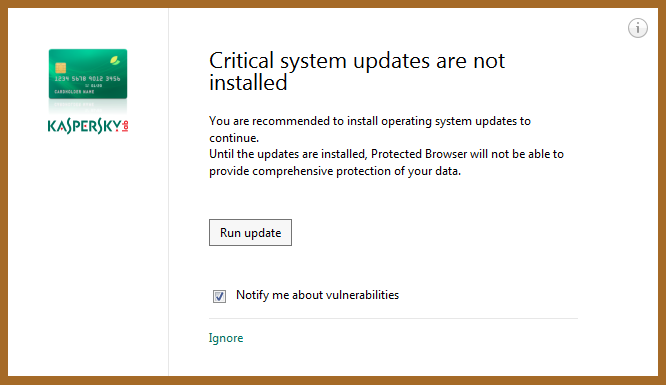
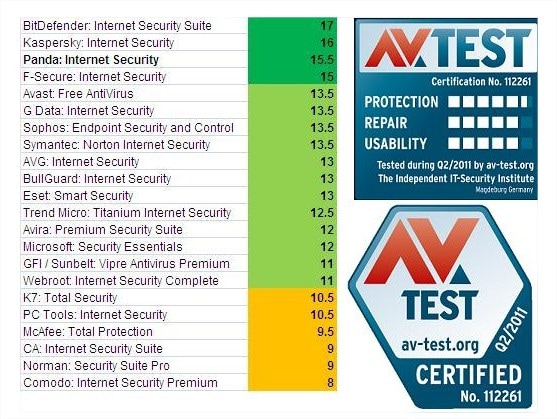
You are probably aware that going online puts you at risk of catching viruses or malware, even if you don’t visit questionable websites. And if you are a careful person, you most likely have a decent antivirus program installed on your computer. Do you believe with all your heart that your computer is safe and your antivirus can protect it against any threat that tries getting through? Think again! There are certain conditions or circumstances, which may lead to a major security breach that may result in an infection or data loss. Even if you believe you are well protected, read on to see the top 5 reasons your antivirus may fail to protect your computer. 1. License Expired Oftentimes, when you buy a new computer, it comes with some antivirus program preinstalled on it. And most of the time it is a 30-day trial that requires you to purchase a license after 30 days, which a clear majority of users fail to do on time. Same goes for a regular antivirus license, which is normally good for 1 year and which a lot of users fail to renew before the year ends. Both situations lead to your PC remaining without proper protection until you renew your license or buy/install a different antivirus program. The antivirus program you have may still work with the expired license: it may let you run scans and even clean up threats, but it will usually NOT allow you to update virus definitions. This means that malware and viruses released after your license expiration date will not be detected. Make sure your antivirus license is active and don’t let your PC go even for a day with no AV protection when your license expires: renew or replace beforehand. 2. No Updates Installed Some security programs require you to run database updates manually or you may have set up the program to require manual database updating. Either way, your antivirus will not be aware of the latest viruses and will not detect them if you don’t update the virus definitions database. And the sad truth is that not very many users understand the importance of this task. You’ll be surprised at how many users have antivirus programs on their PC’s using outdated virus databases. All those computers are at risk of getting infected anytime. Have your antivirus program set up to automatically update its virus database when needed. If that’s not possible, update the database manually every day or think of getting a different antivirus that offers automatic updates. 3. You come across malware not covered by antivirus What? Yes, you read it right. There are a lot of users out there who install some other kind of software, such as a disk cleanup program or a PC optimization suite and believe that it is going to protect their computer from viruses and malware. The reason for such a misunderstanding is unclear. It may be because advertisements for that software include the word “protection” and the user automatically thinks it has something to do with viruses, while the software may merely protect PC from glitches, protect data from accidental loss (as in backup software), etc. When their PC gets infected with malware, the user is genuinely surprised and blames that program, while the program wasn’t even meant as an antivirus. Please don’t consider this an insult, but do check your antivirus software to make sure it is what you believe it to be. 5. Your antivirus is not the best And the last reason we will mention here is the simple fact that your antivirus may not be the best one out there. Not all security programs are created equal. When you look at various independent comparative tests of antivirus products, you may see detection rates of anywhere from about 70% to 100%. What does that mean? It means that a program with a 70% detection rate misses 30% of threats, as simple as that. Look at comparative tests and see where your antivirus program stands in their charts. 95% detection rate is considered good, 98% is awesome. Basically, the closer the program is to 100%, the better. If the security program you have on your PC is located low on the chart, your PC may be at a higher risk of getting infected. Consider replacing the program with another one from higher up on the chart.
Learn how to check whether a site is legitimate: read user reviews and see what independent sources say about the site. Have your antivirus scan any unknown link that you are about to click on. Besides eliminating the five factors we mentioned above, what else can you do to prevent getting infected? The most important thing you can do is learn some safe browsing habits. A recent Google Phishing scam hit headlines after a number of Gmail users had their accounts compromised by a worryingly sophisticated email scam. Users were tricked into clicking an email that took the user to a real Google account selection screen, and after selecting their account, a “Google Docs” window would appear, requesting permission to read, write and access emails.
By granting “Google Docs” permission, the document was revealed to be published by a random Gmail account, and the holder of the account would now have access to the affected account. What they thought was “Google Docs” was in fact a malicious third-party web app, and scammers now had access to user emails, and could send more scam emails from the victim’s account. The most worrying aspect of this phishing scam was that the scam worked within the existing Google login system, it bypassed the two-factor authentication and was only noticeable as fake after clicking the link. The scam took advantage of the fact that fake applications named “Google Docs” can be created, and since the scam didn’t require victims to type in their passwords, the usual anti-phishing measures didn’t block it. The scam exploited Open Authorisation (OAuth). OAuth notifies a resource provider that the resource owner grants third-party access to their information. An example of this would be Facebook (resource provider) being notified that you (resource owner) are allowing a third-party (a Facebook application) to access your information (your friend list). There are a multitude of online services that use OAuth, and it’s impossible to vet all the third-party applications that use it. Fortunately, the scam was detected and dealt with quickly by Google within an hour. A company statement assured users of the following:
Phishing scams of this scale are relatively rare, and therefore make headline news. However, phishing attacks are all too common and it’s worth taking preventative measures to ensure that your account isn’t compromised. How to Protect Yourself from a Phishing Scam Phishing emails are typically designed to fool the victim into giving away their personal information, or installing malicious software. Luckily, there are a few easy ways to spot a phishing scam:
But regardless of how vigilant you might be when inspecting your emails, mistakes do happen and the most convincing scams often fool even the savviest of tech users. Our next post will cover the next steps should your system fall prey to a phishing scam, with tips on how to locate the affected account, and investigate what data has been accessed. |
Archives
November 2023
|
|
2951 Britannia crescent
Port Coquitlam BC, V3B 4V5 778-776-6222 Hours of operation Mon - Fri 9 a.m. - 6 p.m. Sat 11 a.m. - 5 p.m. (by appointment only) Sunday & Holidays - Closed |
Business Number 778569517BC0001 - © Copyright CompuBC, All Rights Reserved.
|