|
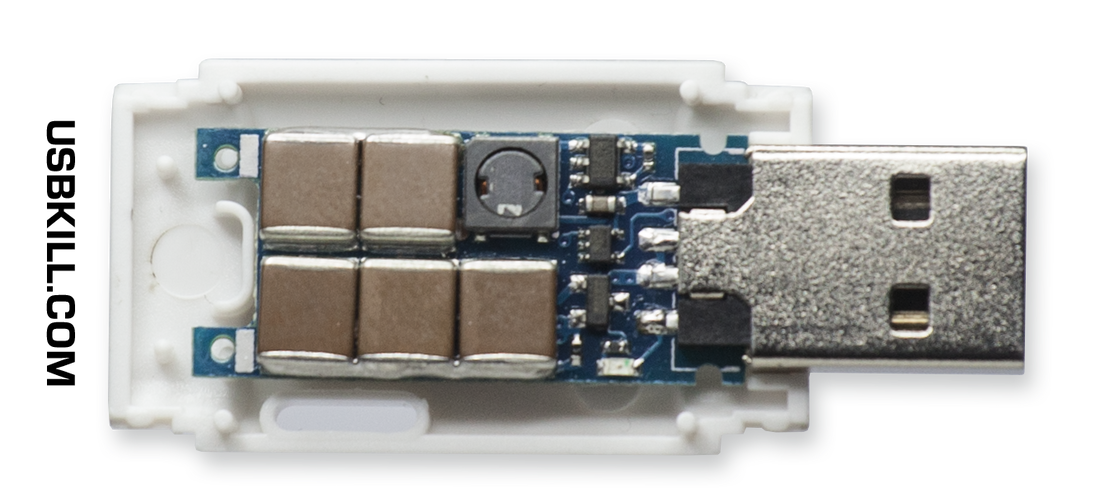
Did you find a random USB stick, perhaps at your school or in a parking lot? You may be tempted to plug it into your PC, but you could leave yourself open to attack or, worse still, permanently damage your machine. Here’s why. USB Sticks Can Spread Malware Probably the most common threat posed by a USB drive is malware. Infection via this method can be intentional and unintentional, depending on the malware in question. USB drives can also disseminate other security threats like remote access trojans (RATs), which give a potential attacker direct control of the target, keyloggers that monitor keystrokes to steal credentials, and ransomware that demands money in exchange for access to your operating system or data. Ransomware is an increasing problem, and USB-based attacks aren’t uncommon. In early 2022 the FBI released details about a group called FIN7 who were mailing USB drives to US companies. The group attempted to impersonate the US Department of Health and Human Services by including the USB devices with letters referencing COVID-19 guidelines and sent some infected drives out in Amazon-branded gift boxes with thank you notes and counterfeit gift cards. In this attack, the USB drives presented themselves to the target computer like keyboards, sending keystrokes that executed PowerShell commands. In addition to installing ransomware like BlackMatter and Ravil, the FBI reported that the group could obtain administrative access to target machines. In addition to USB drives being used to deliver a payload, dreams can just as quickly become infected by being placed into compromised computers. These newly infected USB devices are then used as vectors to infect more machines, like your own. This is how it’s possible to pick up malware from public machines, like those you might find in a public library. “USB Killers” Can Fry Your Computer While malicious software delivered by USB poses a real threat to your computer and data, there is a potentially even greater significant out there in the form of “USB killers” that can physically damage your computer. These devices created quite the splash in the mid-2010s, with the most famous being the USBKill which is (at the time of writing) on its fourth iteration. This device (and others like it) discharges power into whatever it is plugged into, causing permanent damage. Unlike a software attack, a “USB killer” is designed to damage the target device at a hardware level. Data recovery from drives may be possible, but components like the USB controller and motherboard will probably not survive the attack. USBKill claims that 95% of devices are vulnerable to such an attack. These devices don’t only affect your computer via USB drives. Still, they can also deliver a powerful shock to other ports, including smartphones that use proprietary ports (like Apple’s Lightning connector), smart TVs and monitors (even over DisplayPort), and network devices. While early versions of the USBKill “pentesting device” repurposed the power supplied by the target computer, newer versions contain internal batteries that can be used even against devices that aren’t powered on. The USBKill V4 is a branded security tool used by private companies, defense firms, and law enforcement worldwide. We found similar unbranded devices for less than $9 on AliExpress, which look like standard flash drives. These are the thumb drives you are far more likely to encounter in the wild, with no real tell-tale signs of the damage they can cause. How to Deal With Potentially Dangerous USB Devices The simplest way of keeping your devices safe from harm is to scrutinize every device you connect. If you don’t know where a drive came from, don’t touch it. Stick to brand-new drives that you own and purchased yourself, and keep them exclusive to devices that you trust. This means not using them with public computers that could be compromised While USB killers could cost you hundreds or thousands of dollars in hardware damage, you’re probably not likely to encounter one unless someone targets explicitly you. Malware can ruin your whole day or week, and some ransomware will take your money and then destroy your data and operating system anyway. Some malware is designed to encrypt your data to make it unrecoverable, and the best defense against any type of data loss is to always have a solid backup solution. Ideally, you should have at least one local and one remote backup. If sharing drives are unavoidable, make sure other parties are aware of the dangers and take steps to protect themselves (and you, by extension). Running anti-malware software is a good start, mainly if you’re using Windows. Take Care For most people, malware delivered by USB poses little threat because cloud storage has replaced physical devices. “USB killers” are scary-sounding devices, but you probably won’t encounter one. However, by taking simple precautions like not putting random USB drives into your computer, you can eliminate almost all risks. However, it would be naive to assume that attacks of this nature do occur. Sometimes they target individuals by name, delivered in the post. Other times they’re state-sanctioned cyberattacks that damage infrastructure on a massive scale. Stick to a few general security rules and be safe online and offline. On a personal note
"Your problem is our problem." don't be the weakest link; think before clicking, opening, inserting, and executing. Once you introduce any type of risk into a network, it will become a greater risk to us all.
0 Comments
|
Archives
November 2023
|
|
2951 Britannia crescent
Port Coquitlam BC, V3B 4V5 778-776-6222 Hours of operation Mon - Fri 9 a.m. - 6 p.m. Sat 11 a.m. - 5 p.m. (by appointment only) Sunday & Holidays - Closed |
Business Number 778569517BC0001 - © Copyright CompuBC, All Rights Reserved.
|