|
What Is 'Catfishing'?
“Catfishing’ refers to a scam where someone, the ‘catfish,’ creates a fictitious online identity and seeks out online relationships. These are frequently romantic relationships, and online dating websites and cell phone dating apps are fertile hunting ground for catfish. However, there are also catfish who seek out friendships and other forms of social contact. Catfishing involves significant deception – it’s not just someone fudging his or her height and weight in a Match.com profile and using a three-year-old photo. A catfish will be far more deceptive. Often, he or she will use someone else’s photos; grab personal details such as work, educational history, and personal histories off of the Internet; and invent an entirely fictitious life for his or her fictitious identity. The growing popularity of online dating has made catfishing more and more common. Estimates for catfishing victims are in the thousands, and that number is probably under representative. Catfishing victims can be deeply embarrassed and many don’t talk share or talk about it. What Do ‘Catfish’ Want? There’s not necessarily a catch to catfishing. A catfish is often just someone pretending to be someone they’re not using the anonymity of the Internet. He or she might may have low self-esteem and build a fictitious online persona to interact with people. Or a catfish might simply find their deception amusing. More malicious motives can exist as well. Some catfish seek money, and build a fake relationship with their victims to get it. Others seek to prey on their victims’ sympathies and emotions, often relating tragic family events or personal circumstances. Catfish have also been known to seek revenge on a former significant other, prank a friend or acquaintance, or simply seek to amuse themselves at the expense of other people. ‘Catfishing’ in Popular Culture ‘Catfishing’ has been prominently featured in popular culture. The term itself comes from Catfish, a 2010 movie that featured a man meeting a woman online before growing concerned about her true identity. The movie led to a spin-off, Catfish: The TV Show, on MTV. Probably the most widely known catfishing case involved Manti Te’o, a University of Notre Dame football star. His girlfriend supposedly died of leukemia mid-season, leading to heart-warming tributes and media attention. Only later was it determined that his supposed, online girlfriend never existed. Her entire identity was faked. How Can I Recognize ‘Catfishing’ Online? ‘Catfishing’ boils down to someone maintaining a fake online profile. You can find tips for recognizing catfish on dating websites and advice columns across the Internet, but here are some common signs:
If you think someone you’re talking to online might not be who they say they are, there are a few things you can do:
CTV News: Canadians lost $17M to online dating scams last year WHAT ARE THE DIFFERENT TYPES OF ONLINE CATFISH? ONLINE DATING CATFISH This is one of the newest and most recently publicized catfishing scams although, they’ve been going on a lot longer than people know about. Typically, the catfish reaches out to a person through a forum or social network (like Facebook or a dating site like pof.com, OKCupid, etc.) and engages conversation with them. The catfish will create fake profiles and oftentimes elaborate stories to keep the charade going. There are different things that motivate each of these people. It’s most commonly a need to be liked, hide who they really are because of confidence issue and sometimes it’s because of greed because they want your money but, in all cases, the catfish is lying about who they are. NIGERIAN PRINCE SCAM This is one of the oldest and most known catfishing profiles that originally started with mail then, fax and then email. The story has evolved over time from needing money to get the prince out of jail and then personal information in order to wire money but, the most recent story is the African prince needs money for bribes so that they can get access to the money and in return, they (the scam artist) claim that they will provide a large payoff. Another version of this story is that the prince needs to store the money temporarily in order to hide the money. They ask for personal bank information in order to transfer the money and then steal money. The latest version of this scam are people posing as your relatives on Facebook telling you that they know a wealthy person that needs money because to move because they don’t currently have access to their money. These are the worst types of the catfish scams and always involved a request for personal information or to send money. RUSSIAN BRIDES SCAM (ROMANCE SCAM) This is one of the easiest scams to catch but, so many people fall for it each year because it plays into their emotions. A typical Russian bride scam plays out where you are contacted by a women (it can be a man too) who is looking for an American mate to marry and settle down with. After a specified time, they start asking for money for things like internet (because it’s supposedly expensive in their country) plane tickets, travels expenses, etc. Another example is where the scammer will contact you, start developing feelings really quickly and then disappear. Once they reappear, they tell you that they’ve been in a horrible accident and that they need money for medical expenses, etc. These types of scams always involve asking for money to help them pay for things that can be narrowed down to medical expenses, travel costs or basic necessitates. Keep in mind that they don’t always come from Russia
0 Comments
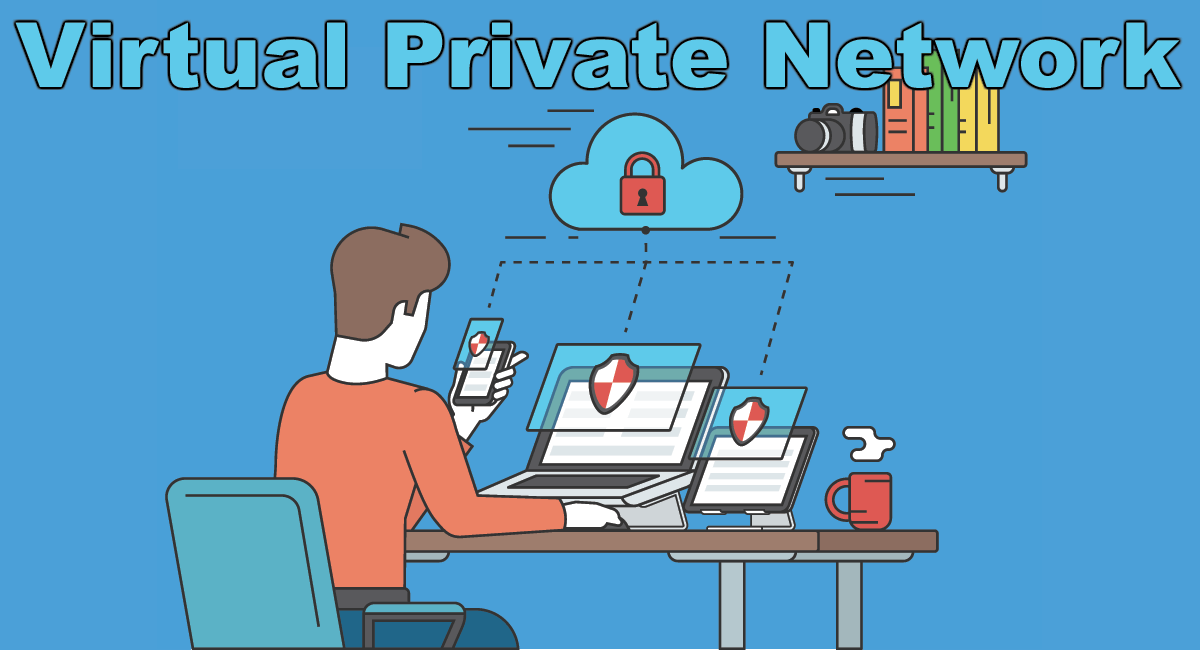
VPN or virtual private network is one of the popular choices for commercial employees, as it helps them to access and work on a secured network. There are a lot of software and applications available in the market, which can be bought and used on a regular basis. VPN is a more like a framework, which is meant for its security and easy access for people. The virtual private network used to come with an electronic gadget called FOB, which provides a unique set of number for people to enter to use the network. The VPN access would need internet connectivity to get connected, as VPN is like any other software or an application available in the market. VPN or virtual private network is one of the popular choices for commercial employees, as it helps them to access and work on a secured network. There are a lot of software and applications available in the market, which can be bought and used on a regular basis. VPN is a more like a framework, which is meant for its security and easy access for people. The virtual private network used to come with an electronic gadget called FOB, which provides a unique set of number for people to enter to use the network. The VPN access would need internet connectivity to get connected, as VPN is like any other software or an application available in the market. There are a lot of VPN available to buy at different costs and they are available with different features suitable for users and organizations. The encrypted interface lets people access different websites and tools without getting compromised on the security. Some Of The Popular VPN Service Providers In The MarketExpress VPN – Express VPN is one of the most sought software, which has been used worldwide in most of the organizations. The tool is considered as extremely reliable and super fast in terms of performance and known for its perfect streaming features. The security and the super fast feature have been widely appreciated, as most of the organizations prefer to use Express VPN for total privacy.
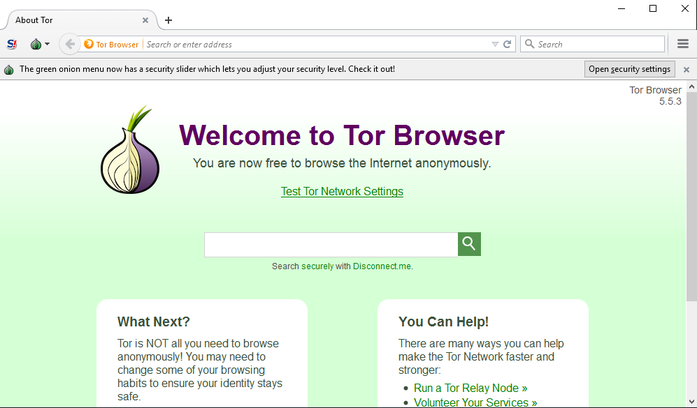
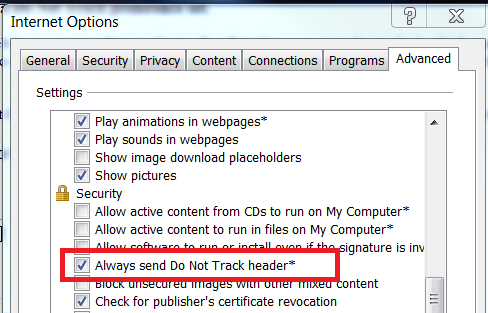
Nord VPN – Nord VPN is best used in IT and Media industry, which provides top-level security to users and ensure to support users around the clock. The customer or technical support is available through different sources like phone, EMAIL, and live chat. A great balance between security and assistance can help you to access your network in a secure environment. The VPN software has been rated 9 out of 10 and has become favorite software for people, who are looking forward to experiencing a secured network. IP Vanish – IP vanish can be considered as the fastest VPN software, as it can be used at any location with an internet connectivity. IP Vanish is ideal for people, who are looking out to use VPN software with a lot of privacy. The best part of IP vanish is, it does not use 3rd party servers and provides complete security round the clock. IP Vanish has the ability to connect to 850+ VPN servicers in over more than 60 countries easily, which enhances your experience in web surfing and a quick access to the server. GOM – GOM is one of the popular VPN software, which has been used widely in most of the countries. GOM has a special feature, which detects a blocked website across the world and can perform the same task accurately in Singapore. GOM has the capability to activate the VPN automatically and provides complete security while accessing the tool. The user interface has been widely appreciated, as it provides a user-friendly screen to navigate across different options in the software. The automatic features help people to turn ON and OFF at any given point of time in an automatic way. Pure VPN – Pure VPN is one of the most preferred among security professionals, which comes with a broad range of service locations. The server locations are worldwide, which includes mainland China. The Pure VPN provides a quality customer and technical support to people at any given point of time, as the support is available 24hours and 7 days a week. The customer support is available to take with the help of live chat, which helps you to fix problems instantly. Private Internet Access - Private Internet Access is the leading VPN Service provider specializing in secure, encrypted VPN tunnels which create several layers of privacy and security providing you safety on the internet. Private Internet Access VPN Service is backed by multiple gateways worldwide with VPN Tunnel access in 25+ countries, 37+ regions. The privacy of average internet denizens has never been in greater peril. ISPs, advertisers, and government agencies from around the world are increasingly interested in tracking every single movement you make online. Whether you’re a whistle blower, a political dissident, or simply someone who hates the idea of third-parties scrutinizing your surfing habits, there are plenty of tools available to keep prying eyes off of your traffic. In this post, I'll highlight 19 ways to increase your online privacy. Some methods are more extreme than others, but if you’re serious about maintaining your privacy, these tips will help shield your traffic from snoops. Of course, internet security is a topic in and of itself, so you’re going to need to do some reading to remain thoroughly protected on all fronts. And remember, even the most careful among us are still vulnerable to imperfect technology. GnuPG - Email is notoriously insecure. Even if you're connecting to your email server over an SSL connection, there's a good chance that your message can be intercepted on the way to the intended recipient. So if you want to send private messages over email, you're going to need to add a layer of encryption. When you and your recipient use GnuPG (or equivalent tools), you can easily prevent simple snooping. Of course, it's always possible for vulnerabilities to emerge, but imperfect protection is always better than no protection at all. Tor Browser - If anonymous browsing is what you're after, the Tor Browser is what you need. It uses a vast network of computers to route your Web traffic through a number of encrypted layers to obscure its origin. Tor is a vital tool for political dissidents and whistleblowers to anonymously share information, and you can just as easily use it to help protect your privacy. This customized fork of Firefox automatically connects to the Tor network, and includes some of the privacy-enhancing browser extensions discussed later in this post. This package has everything you need to use Tor successfully, but you'll also need to change your web surfing behavior to retain as much anonymity as possible. Abide by the Tor warnings, and remember this isn't a magic bullet. VPN - If you're very serious about maintaining your anonymity, consider investing in a VPN solution like TorGuard or Private Internet Access. While the protection isn't perfect, they will help you to disguise your activities online. Your real IP address will be hidden from the world, and your traffic will remain indecipherable to nosy ISPs or governments. Even if your country is actively on the lookout for VPN traffic, you can still benefit from so-called "stealth VPNs." TorGuard offers its stealth VPN service at no additional cost, and it will make government detection and interference much harder to accomplish. For those of you being held hostage by your government, VPNs are by far the best bet for bypassing censorship and snooping. DNS Leak Testing - Even if you're using a privacy service like a VPN to hide your IP address, it's still possible to give away clues to your identity via your DNS traffic. Thankfully, it's easy to detect if your configuration is leaking your DNS information. Simply head over to DNSLeakTest.com, and run the extended test. If the results show the third-party DNS service you're using (like TorGuard), you're set. If your ISP's DNS info shows up, you have a DNS leak. Follow the steps listed on the "How to fix a DNS leak" page, and then test yourself again to make sure everything is working as intended. Virtual machines - While the browser is a massive vector for snooping, it isn't the only place that third parties will try to attack. PDFs and other seemingly harmless files can serve as homing beacons, and potentially alert government entities when you're viewing planted contraband. To prevent unintended breaches of privacy, open suspect files inside of a virtual machine. Load up your favorite Linux distribution inside, configure it to your liking, and then save a snapshot of your VM. Next, download your desired file, and then shut off your virtual machine's access to the Internet. Once you're sure that the VM is cut off completely from the network, you can now open the file safely. Read what you need, make notes, and then shut down the VM. Next time you need to view a file inside one, you'll have your snapshot ready to go. Tails Live Operating System - If you want to take privacy beyond a simple VM solution, you can instead boot up a live OS from a CD or USB stick. Knoppix and Ubuntu are good options for normal use, but Tails is custom-built for preserving your privacy and anonymity. Your traffic is automatically routed through Tor, encryption tools are built-in for IM and email, and it won't interact with any of your existing OS installations. It's an excellent all-in-one package that's easy to use. Still, you need to be vigilant. All of the same Tor disclaimers apply, and if you're using this on a shared PC, you could still be tracked with the likes of a simple key logger. Blocking Third-Party Cookies - Third-party cookies are one of the most common methods that advertisers use to track your browsing habits. If you visit two sites using the same advertising service, rest assured that the advertiser is keeping tabs on that information. However, every major Web browser offers the ability to turn off tracking cookies. While this is far from a panacea, it shuts down the most common vector used by advertisers to build usage profiles. No sense making it easy for them, right? Blocking Location Data - In recent years, many sites have begun using location data to offer specific services, and serve targeted advertisements. Mapping applications have legitimate reasons for gathering location data, but that same technique can be used to help identify who you are. Any proper browser should let you toggle on and off location data, and we recommend leaving it off completely. At the very least, demand that websites prompt you for access before gathering the data. That said, IP-based geolocation data is incredibly trivial to acquire, so remain vigilant. If you're browsing the Web without a proxy or a VPN, you're effectively broadcasting your IP to every server you come across, and that information can be used against you. It's not necessarily something you have to worry about constantly, but it's worth keeping that fact in the back of your mind if you're criticizing your local dictator or blowing a whistle on the NSA. Do Not Track - The "Do not track" HTTP header is an optional message that browsers can send to Web servers. You can easily enable it in your browser's settings, but it's rather limited in scope. For this to work at all, the Web server needs to be configured to respect this flag. There is absolutely no requirement that any website needs to obey this setting, so don't expect widespread protection from trackers. Still, you don't have much to lose. The only potential issue here is that it's an additional datapoint for browser fingerprinting. But if enough people are using it, that shouldn't be a real issue. Plug-In Management - Even if your browser is configured properly to hide your identifying information, plug-ins can still be used to endanger your anonymity. If you're serious about remaining anonymous, you should avoid running plug-ins altogether. Unfortunately, that can leave a number of popular websites completely unusable. To solve this problem, we recommend a hybrid approach. First of all, configure your browser to require your approval to run any plug-in. Next, make sure you're running sandboxed plug-ins. While this is mostly considered a security issue, a rogue plug-in could be used to gather your personal information by an organization like the NSA. Chrome can be configured to completely disallow un-sandboxed plug-ins, but it can be trickier with some other browsers. Windows users can run their browsers inside of an application called Sandboxie, so less sophisticated browsers can receive similar benefits. JavaScript Blocking - JavaScript is incredibly powerful, but that useful little scripting language can be used against you. By design, it can deliver detailed information about your system to any Web server. What plug-ins do you have enabled? What size screen are you using? Those small pieces of information can add up, and make tracking your usage profile easier for advertisers and governments. Worse, unpatched JavaScript exploits could potentially be used to trick your browser into giving up even more identifying information. If you want to be truly anonymous, you're going to need to disable JavaScript. That's easier said than done, since many websites rely on JavaScript for core functionality, so you'd be effectively knee-capping your Web browser. But when you use extensions like NoScript, you can manually manage which domains have permission to run JavaScript in your browser. This way, you can whitelist only the domains and webpages that you absolutely trust. Privacy Badger - If you're looking for a Popeil-esque "set it and forget it" method of blocking trackers online, try out the EFF's Privacy Badger add-on. Available for Chrome, Firefox, and Opera, this browser extension monitors when sites try to track your browsing habits, and automatically thwarts future tracking attempts. While this add-on was built using the Ad-Block Plus codebase, this isn't truly an ad-blocking tool. Instead, the EFF is only interested in blocking snoops. Best of all, the list of blocked content automatically improves as you browse -- no need to manually block trackers. HTTPS Everywhere - In spite of some infamous security issues, SSL is still extremely important for keeping your Web traffic safe from prying eyes. If you want to keep nosy packet sniffers out of your business, your Web traffic should always be going through SSL connections. Sadly, not every website supports SSL. Even worse, many websites that do support SSL still default to unencrypted connections -- and the Electronic Frontier Foundation wants to change that. The HTTPS Everywhere browser extension, provided for free by the EFF, forces SSL connections on countless websites. Chrome, Firefox, and Opera users can all take advantage of this wonderful extension, and keep important Web traffic private and secure. Thwart Search Engine Tracking URLs - It's no secret that Google makes money by tracking your behavior for targeted ads, and that's problematic from a privacy perspective. Using DuckDuckGo is a good alternative for some of us, but the quality of Google's results can be difficult to forgo. Thankfully, you can easily sidestep one of Google's most obnoxious behaviors: URL trackers. When you click on a URL in Google, it actually loads a redirect URL first for easier tracking. Even worse, simply copying the link from Google can give you a long, messy tracking link instead of the plain URL you really want. But when you use this simple little Firefox extension called Searchlinkfix, it does away with that completely. Disable WebRTC - Did you know that your browser can leak some of your network information to any web server that asks for it? If your browser has WebRTC enabled, your internal IP can be accessed by any given website, and it can potentially reveal your real IP address while using a VPN. If you're using Firefox, you can go into about:config, and set media.peerconnection.enabled to "false." Alternately, you can use the popular content blocker uBlock Origin to turn off this functionality in Chrome and Firefox. BetterPrivacy - Even if you're blocking traditional cookies, some sites can still track you using LSOs (Local Shared Objects) -- commonly known as "Flash cookies." If you never use Flash, these won't be a problem, but that can be incredibly difficult to pull off for some of us. Of course, you could configure Flash to block all LSOs, but that would break some Flash content. Thankfully, there is a simple plug-in for Firefox called BetterPrivacy that allows you to granularly manage your LSOs just as you would with normal cookies. Browser Leak Testing - Is your browser disclosing personally identifiable information? Head over to BrowserLeaks.com, and take a gander at all of the data your browser is giving away. This toolset will never be completely exhaustive, but if you want to verify that your privacy and security precautions are really working, this site is an invaluable asset. Panopticlick - Depending on how your browser is configured, there's a chance that online advertising giants and nosy government agencies can identify your browsing behavior by recognizing just a few telltale markers. To discover exactly how unique your browser's fingerprint is, head on over to Panopticlick. This handy little tool, owned and operated by the Electronic Frontier Foundation, quickly tells you just exactly what your browser is broadcasting to the world. The more information given away, the easier it will be to identify you as a unique individual. Multiple Email Addresses - When you sign-up for user accounts across the web, using a different email address for each site is a good way to throw unscrupulous third-parties off of your trail. If you're merely creating a throwaway account on a whim, consider using disposable email accounts from sites like Mailinator or YopMail. Anybody can access those inboxes though, so use discretion. If you actually want to maintain legitimate accounts on sites like Facebook or Twitter, you can create numerous free email accounts, and then configure email forwarding to funnel all of the messages into a single inbox. It's a lot of additional work, but it also offers the benefit of being able to easily detect which sites are selling your information to spammers. Justified Paranoia You might think that you have nothing to hide, but that doesn’t mean you shouldn’t enjoy the benefits of online privacy. It’s a lot easier to shove your fingers in your ears, and pretend like the NSA and your ISP aren’t watching every move you make. But what you browse is your business, and your business alone. Now is the time to stand up for yourself, and take back your privacy. With the help of Grant Brunner ExtremeTech
|
Archives
November 2023
|
|
2951 Britannia crescent
Port Coquitlam BC, V3B 4V5 778-776-6222 Hours of operation Mon - Fri 9 a.m. - 6 p.m. Sat 11 a.m. - 5 p.m. (by appointment only) Sunday & Holidays - Closed |
Business Number 778569517BC0001 - © Copyright CompuBC, All Rights Reserved.
|