|
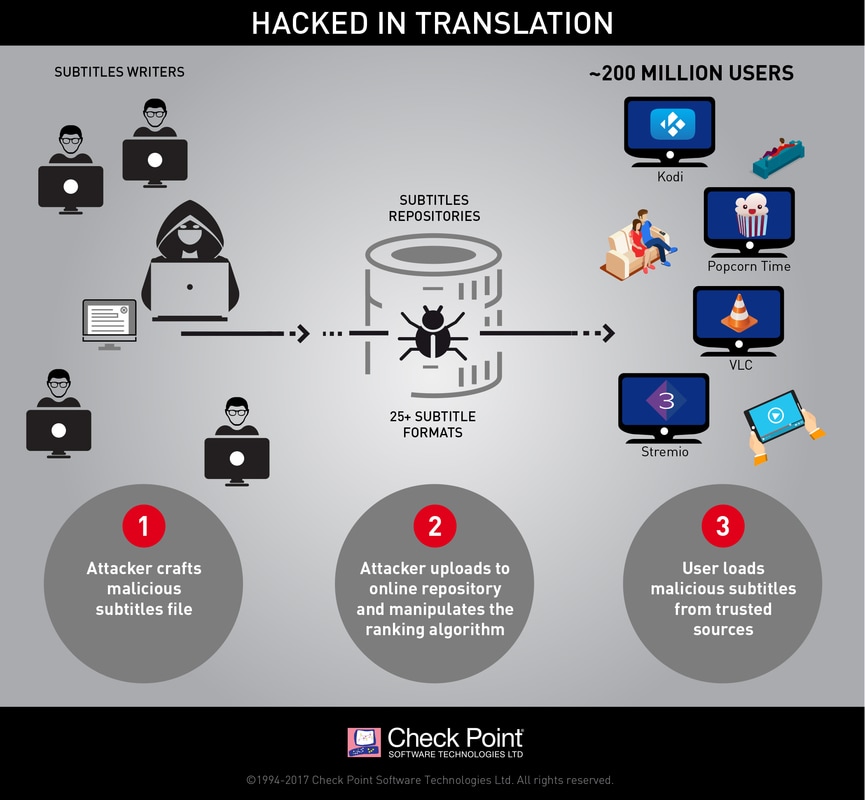
Check Point researchers revealed a new attack vector which threatens millions of users worldwide – attack by subtitles. By crafting malicious subtitle files, which are then downloaded by a victim’s media player, attackers can take complete control over any type of device via vulnerabilities found in many popular streaming platforms, including VLC, Kodi (XBMC), Popcorn-Time and strem.io. We estimate there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years. What is it? Perpetrators use various methods, also referred to as ‘attack vectors’, to deliver cyberattacks. These attack vectors can be divided into two major categories: Either the attacker persuades the user to visit a malicious website, or he tricks him into running a malicious file on his computer. Our research reveals a new possible attack vector, using a completely overlooked technique in which the cyberattack is delivered when movie subtitles are loaded by the user’s media player. These subtitles repositories are, in practice, treated as a trusted source by the user or media player; our research also reveals that those repositories can be manipulated and be made to award the attacker’s malicious subtitles a high score, which results in those specific subtitles being served to the user. This method requires little or no deliberate action on the part of the user, making it all the more dangerous. Unlike traditional attack vectors, which security firms and users are widely aware of, movie subtitles are perceived as nothing more than benign text files. This means users, Anti-Virus software, and other security solutions vet them without trying to assess their real nature, leaving millions of users exposed to this risk. What is the root cause? The attack vector relies heavily on the poor state of security in the way various media players process subtitle files and the large number of subtitle formats. To begin with, there are over 25 subtitle formats in use, each with unique features and capabilities. Media players often need to parse together multiple subtitle formats to ensure coverage and provide a better user experience, with each media player using a different method. Like other, similar situations which involve fragmented software, this results in numerous distinct vulnerabilities. What’s the effect? Scope: The total number of the affected users is in the hundreds of millions. Each of the media players found to be vulnerable to date has millions of users, and we believe other media players could be vulnerable to similar attacks as well. VLC has over 170 million downloads of its latest version alone, which was released June 5, 2016. Kodi (XBMC) has reached over 10 million unique users per day, and nearly 40 million unique users each month. No current estimates exist for Popcorn Time usage, but it’s safe to assume that the number is likewise in the millions. Damage: By conducting attacks through subtitles, hackers can take complete control over any device running them. From this point on, the attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device. The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more. Which media players are affected? To date, we tested and found vulnerabilities in four of the most prominent media players: VLC, Kodi, Popcorn Time and Stremio. We have reason to believe similar vulnerabilities exist in other media players as well. We followed the responsible disclosure guidelines and reported all vulnerabilities and exploits to the developers of the vulnerable media players. Some of the issues were already fixed, while others are still under investigation. To allow the developers more time to address the vulnerabilities, we’ve decided not to publish any further technical details at this point. Platforms Update:
IPS Signatures:
How can this attack vector spread? Delving even further into the subtitle supply chain produced some interesting results. There are a number of shared online repositories, such as OpenSubtitles.org, that index and rank movie subtitles. Some media players download subtitles automatically; these repositories hold extensive potential for attackers. Our researchers were also able to show that by manipulating the website’s ranking algorithm, we could guarantee crafted malicious subtitles would be those automatically downloaded by the media player, allowing a hacker to take complete control over the entire subtitle supply chain, without resorting to a Man in the Middle attack or requiring user interaction. This vulnerability also affects users who use these rankings to decide which subtitles to download manually. 2017-07-13 You may be aware that TVaddons.ag has been taken offline, TVAddons was one of the largest repositories of Kodi add-ons. Ian Garland from Comparitech posted an alternative to TVaddons.ag with some useful add-ons. I would like to thank Jeff Grant for bringing this to my attestation. You can find the article here: TVAddons.ag down: These are the best Fusion and Indigo add-on alternatives
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
Archives
November 2023
|
|
2951 Britannia crescent
Port Coquitlam BC, V3B 4V5 778-776-6222 Hours of operation Mon - Fri 9 a.m. - 6 p.m. Sat 11 a.m. - 5 p.m. (by appointment only) Sunday & Holidays - Closed |
Business Number 778569517BC0001 - © Copyright CompuBC, All Rights Reserved.
|